Tailscale: A Modern Zero-Trust Networking Platform Built on WireGuard
Introduction
Traditional VPNs were designed for a different era — static offices, trusted internal networks, and perimeter-based security. Today’s reality is the opposite: remote teams, cloud workloads, SaaS sprawl, home networks, and devices scattered across the internet.
Tailscale rethinks networking from first principles. Instead of “connecting to a network,” it connects identities to devices, using strong cryptography, automatic NAT traversal, and zero-trust access controls — all without managing VPN appliances, firewalls, or complex routing rules.
At its core, Tailscale is a secure, peer-to-peer overlay network built on WireGuard, optimized for simplicity, scalability, and security.
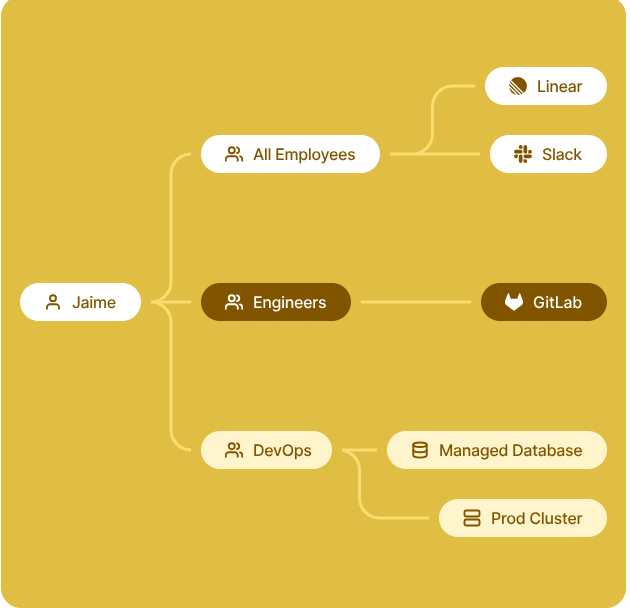
Tailscale – Identity based access to anything
Tailscale is a software-defined private network that creates a secure mesh between devices (“nodes”), allowing them to communicate as if they were on the same LAN — regardless of where they are located.
Key characteristics:
- Zero-trust by default
- Identity-based access
- Peer-to-peer encrypted connections
- No inbound firewall rules required
- Works across clouds, offices, and home networks
Unlike traditional VPNs, Tailscale does not rely on a central traffic hub. Most traffic flows directly between endpoints.
Core Architecture
1. WireGuard as the Foundation
Tailscale is built on WireGuard, a modern VPN protocol known for:
- Minimal attack surface (~4k lines of code)
- Strong cryptography (ChaCha20, Poly1305, Curve25519)
- High performance and low latency
- Simple configuration model
Tailscale manages WireGuard keys and tunnels automatically, removing the operational burden.
2. Control Plane vs Data Plane
A critical design distinction:
Control Plane (Tailscale Coordination Server)
- Authenticates users and devices
- Distributes public keys and network maps
- Manages ACLs and policies
- Never sees user traffic
Data Plane (Peer-to-Peer Traffic)
- Encrypted WireGuard tunnels
- Direct device-to-device whenever possible
- Relays (DERP servers) used only when NAT traversal fails
This separation ensures privacy and performance.
3. NAT Traversal & DERP
Most devices sit behind NATs and firewalls. Tailscale handles this automatically using:
- UDP hole punching
- STUN-like techniques
- DERP (Detoured Encrypted Routing Protocol) as a fallback relay
DERP:
- End-to-end encrypted
- Used only when direct P2P fails
- Optimized for latency, not bandwidth
Identity-First Networking
Tailscale replaces IP-based trust with identity-based trust.
Identity Providers (SSO)
Tailscale integrates with:
- Azure AD / Entra ID
- Google Workspace
- Okta
- GitHub
- JumpCloud
- Custom OIDC providers
Devices are tied to users and groups, not shared secrets.
Device Identity
Each node:
- Has a unique WireGuard keypair
- Is registered to a user
- Can be tagged (for servers, services, automation)
Example:
alice@company.com → laptop
prod-db-01 → tagged server
Access Control & Zero Trust
ACLs (Access Control Lists)
Tailscale uses a JSON-based policy model that defines who can talk to what.
Example:
{
"acls": [
{
"action": "accept",
"src": ["group:devs"],
"dst": ["tag:servers:22"]
}
]
}
This allows:
- Developers → SSH to servers
- No lateral movement
- Default deny model
Tags & Automation
Tags enable non-human access without tying permissions to individuals.
Common use cases:
- CI/CD runners
- Kubernetes nodes
- Bastion hosts
- Database servers
Tags + ACLs = machine-to-machine zero trust.
Key Features
1. MagicDNS
- Automatic DNS for Tailscale nodes
- Access devices via names instead of IPs
- Optional split-DNS for internal domains
Example:
db01.tailnet-name.ts.net
2. Subnet Routers
Expose an entire private subnet through a Tailscale node.
Use cases:
- Access legacy systems
- On-prem → cloud integration
- Gradual zero-trust migration
Example:
10.0.0.0/24 via subnet-router
3. Exit Nodes
Route internet traffic through a trusted device.
Use cases:
- Secure browsing on public Wi-Fi
- Geo-restricted access
- Compliance routing
4. Funnel (Optional Public Ingress)
Tailscale Funnel allows controlled public exposure of services:
- HTTPS endpoints
- Identity-aware access
- No firewall rules
This blurs the line between VPN and ingress, while staying zero-trust.
5. Kubernetes Integration
Tailscale integrates deeply with Kubernetes:
- Pod-level connectivity
- Service exposure without LoadBalancers
- Identity-based access to clusters
- No overlay CNI replacement required
Security Model
Encryption
- End-to-end encrypted (WireGuard)
- Keys rotated automatically
- No plaintext traffic ever visible to Tailscale
Least Privilege
- Default deny
- Explicit ACLs
- Short-lived auth tokens
Auditing
- Device registration logs
- ACL changes
- Admin actions
Performance Characteristics
- Near-native performance on P2P links
- Low latency due to direct routing
- Efficient fallback when relays are required
- Scales from 2 devices to tens of thousands
Common Use Cases
1. Secure Remote Access
Replace traditional VPNs for:
- SSH
- RDP
- Internal dashboards
- Databases
2. Multi-Cloud Networking
Connect:
- AWS, Azure, GCP
- Without VPC peering
- Without IP overlap issues
3. Dev & Ops Access
- Engineers access prod safely
- No public SSH
- No bastion hosts required
4. IoT & Edge Devices
- NAT-restricted environments
- Secure device management
- No inbound ports
Tailscale vs Traditional VPNs
| Feature | Traditional VPN | Tailscale |
|---|---|---|
| Architecture | Hub-and-spoke | Peer-to-peer |
| Trust model | Network-based | Identity-based |
| Firewall rules | Required | Not required |
| Lateral movement | Easy | Prevented by ACLs |
| Setup complexity | High | Very low |
| Scalability | Limited | High |
Pricing & Deployment Model
- Free tier (personal & small teams)
- Paid plans for:
- Advanced ACLs
- SSO enforcement
- Audit logs
- Large teams
Deployment is agent-based:
- macOS, Windows, Linux
- iOS, Android
- Docker, Kubernetes
When Tailscale Is Not the Right Tool
Tailscale is not ideal if:
- You need a public CDN or WAF
- You want anonymous public access
- You require Layer-7 traffic inspection at the edge
In those cases, pair it with tools like Cloudflare or NGINX.
The Big Picture
Tailscale represents a shift from:
“Put everything on the same network”
to
“Grant access only to what’s needed, based on identity.”
It removes the operational pain of VPNs while delivering stronger security, better performance, and vastly improved developer experience.
Tailscale | Secure Connectivity for AI, IoT & Multi-Cloud
Homelab Networking Setup | Securely Connect Devices & Services with Tailscale
